On September 10th Apple unveiled its latest flagship phone , the iPhone 5s. The new flagship device sports a new Apple A7 processor combined with M7 Motion Coprocessor and improved camera with true-tone flash and a lot more.Vignesh had mentioned in the Apple’s iPhone Event round up that the “S” definitely stands for Security , Let’s talk security on the iPhone 5s.

One of the biggest breakthroughs is that Apple has integrated a fingerprint sensor into the same body of the iPhone 5.This is pure engineering, the device’s internal components have been adjusted the right way to have better performance and works flawless. During the keynote it was said that the iPhone 5s has “40x CPU performance” and “56x faster graphics”. The battery life hasn’t reduced after packing so much raw processing power into a device with a 64-bit chip. The fingerprint sensor called “Touch ID” is a foray into the biometric security on Smartphones. It isn’t military grade but it works very simple. No finger slide over the sensor or obtrusive design , Just touch to unlock. This is a fingerprint sensor on the Smartphone done right.
Phil Schiller explained the fingerprint sensor in detail:
“It’s a touch-capacitive sensor. It’s super-thin — it’s 170 microns thin, that’s just thicker than a human hair — yet it’s very high resolution: 500 pixels per inch. You can turn your finger and read it in any orientation.”
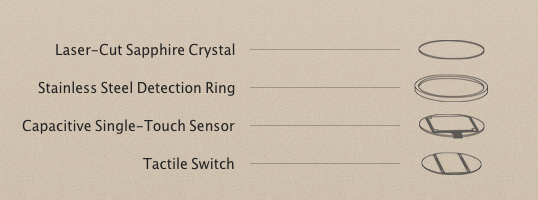
The Touch ID is built into the home button and there is no visible fingerprint sensor, the design is seamless. The home button is now a cover made from sapphire crystal which protects the sensor and acts as lens to precisely focus the sensor to your finger, the stainless steel ring around the buttons is used for detection of a finger and activates the sensor.
The scanned fingerprint is stored on a “Secure Enclave” in the brand new Apple’s A7 processor. When the Touch ID was presented during the keynote , it was clearly mentioned that this fingerprint data is “Never Available to other software, never stored on Apple’s server and never backed up to iCloud”.
Brian Roemmele explained about Secure Enclave on Quora
Apple not only has developed one of the most accurate mass produced biometric security devices, there have also solved critical problems with how the data from this device will be encrypted, stored and secured. Apple Calls this the “Secure Enclave”
How Does The Secure Enclave Work?
It turns out this was the perfect convergence for the synergy needed to allow Apple to move forward with TouchID. Apple has customized a highly optimized version of TrustZone and created what is now known Secure Enclave. Of course Apple will likely never release the details of what they do in the custom hardware for number of reasons. Thus speak directly of TrustZone and extrapolate.
The security of the TrustZone system is achieved by partitioning all of the hardware and software resources so that they exist in one of two worlds – the Secure world for the security subsystem or the Normal world for everything else. The TrustZone-enabled AMBA3 AXI bus fabric ensures that Normal world components do not access Secure world resources, enabling construction of a strong perimeter boundary between the two.
Hardware Architecture of TrustZone.
This design places the sensitive resources in the Secure world, and implements robust software running on the secure processor cores, can protect assets against many possible attacks, including those which are normally difficult to secure. By separating security sensitive peripherals through hardware this will limit the number of sub-systems that need to go through security evaluation. The two virtual processors context switch via a processor mode called monitor mode when changing the currently running virtual processor.
Software Architecture of TrustZone
Check the post on Quora – What is Apple’s Secure Enclave and Why is it Important ?